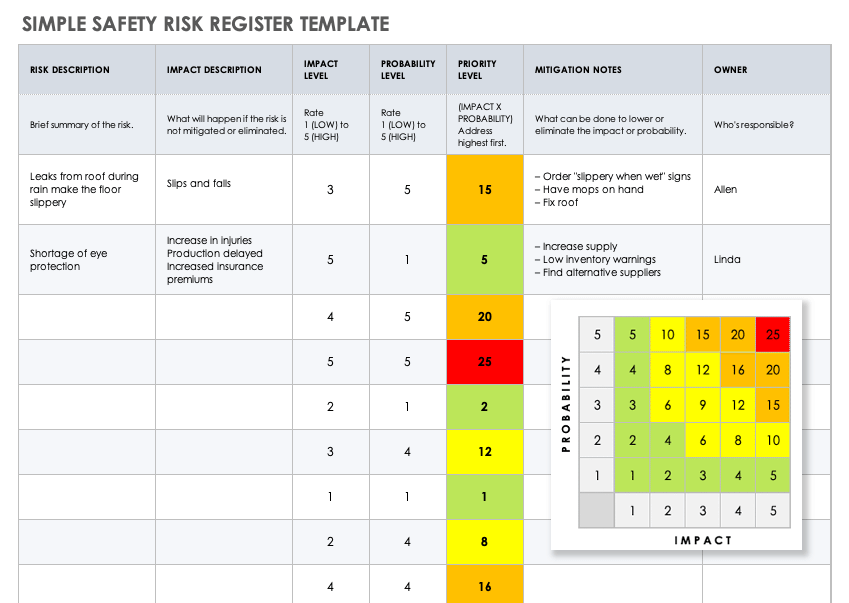
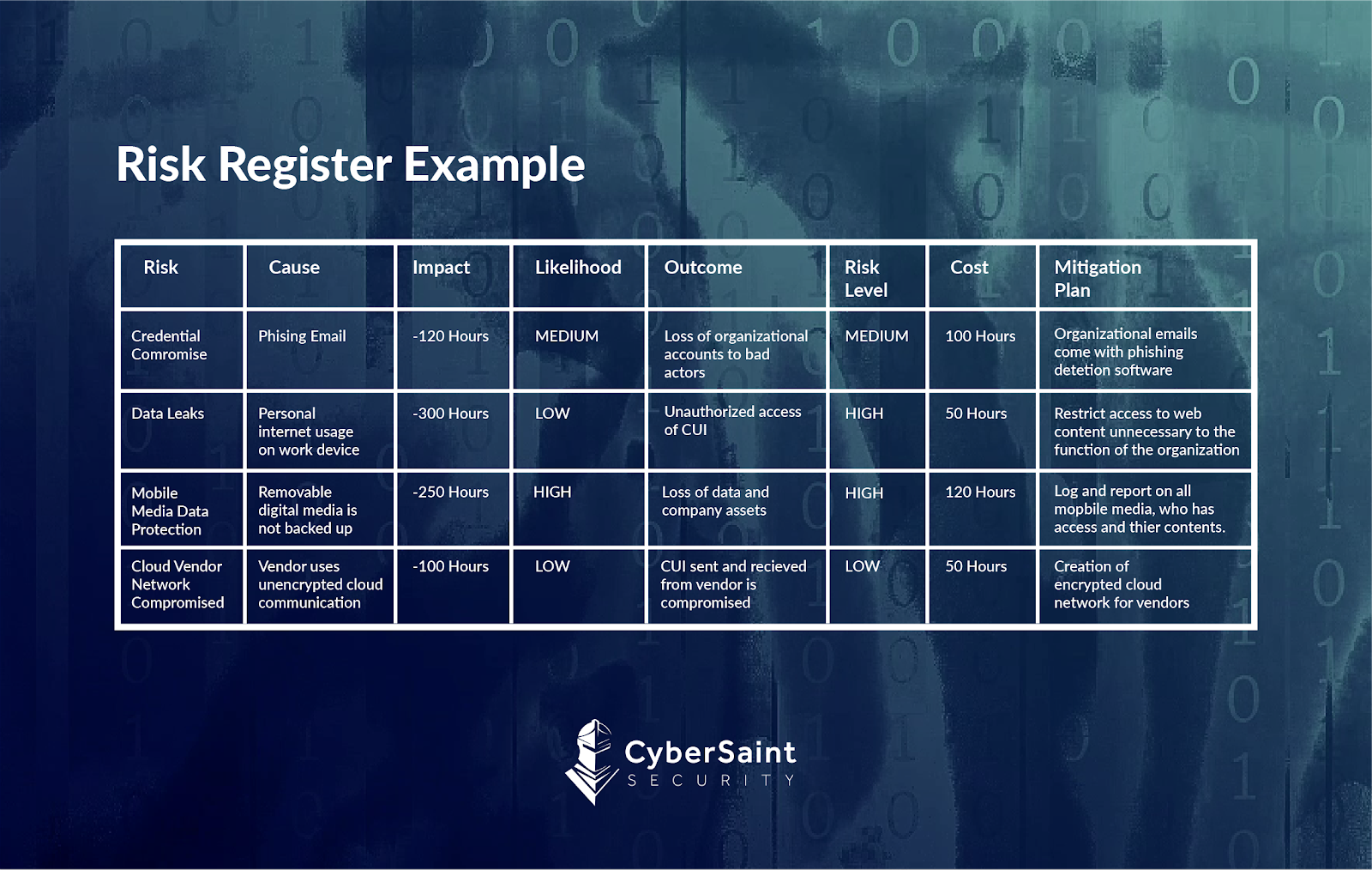
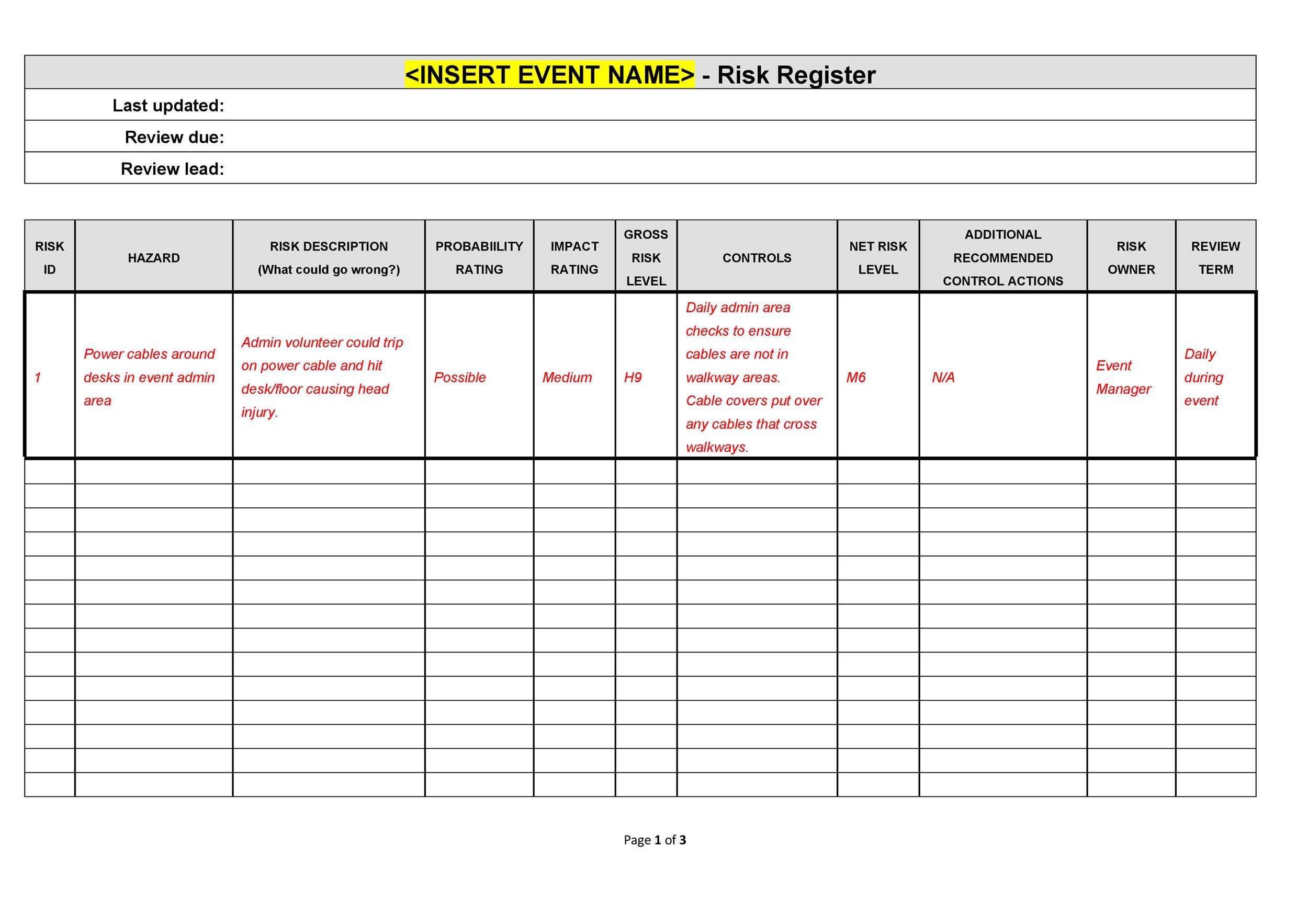
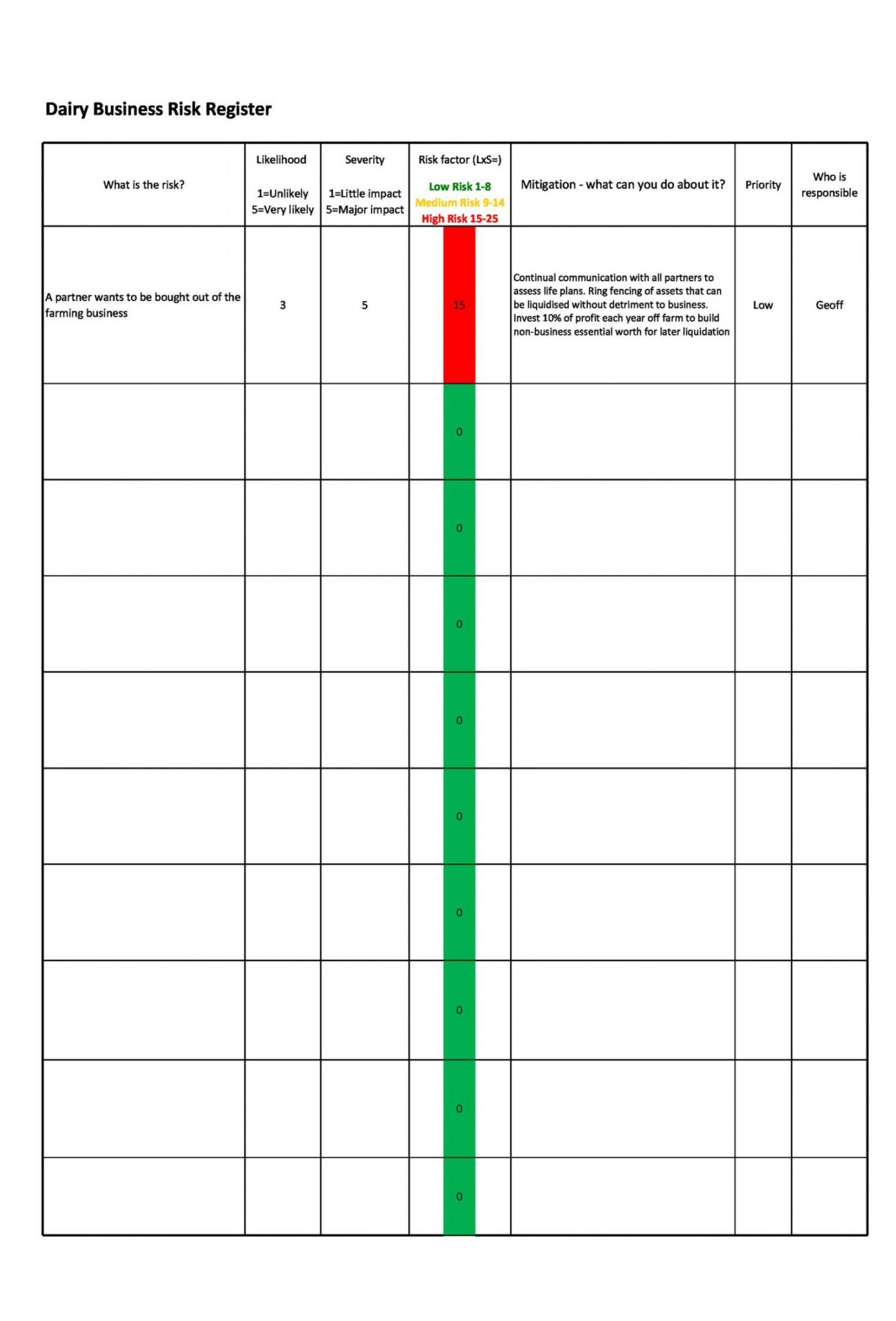
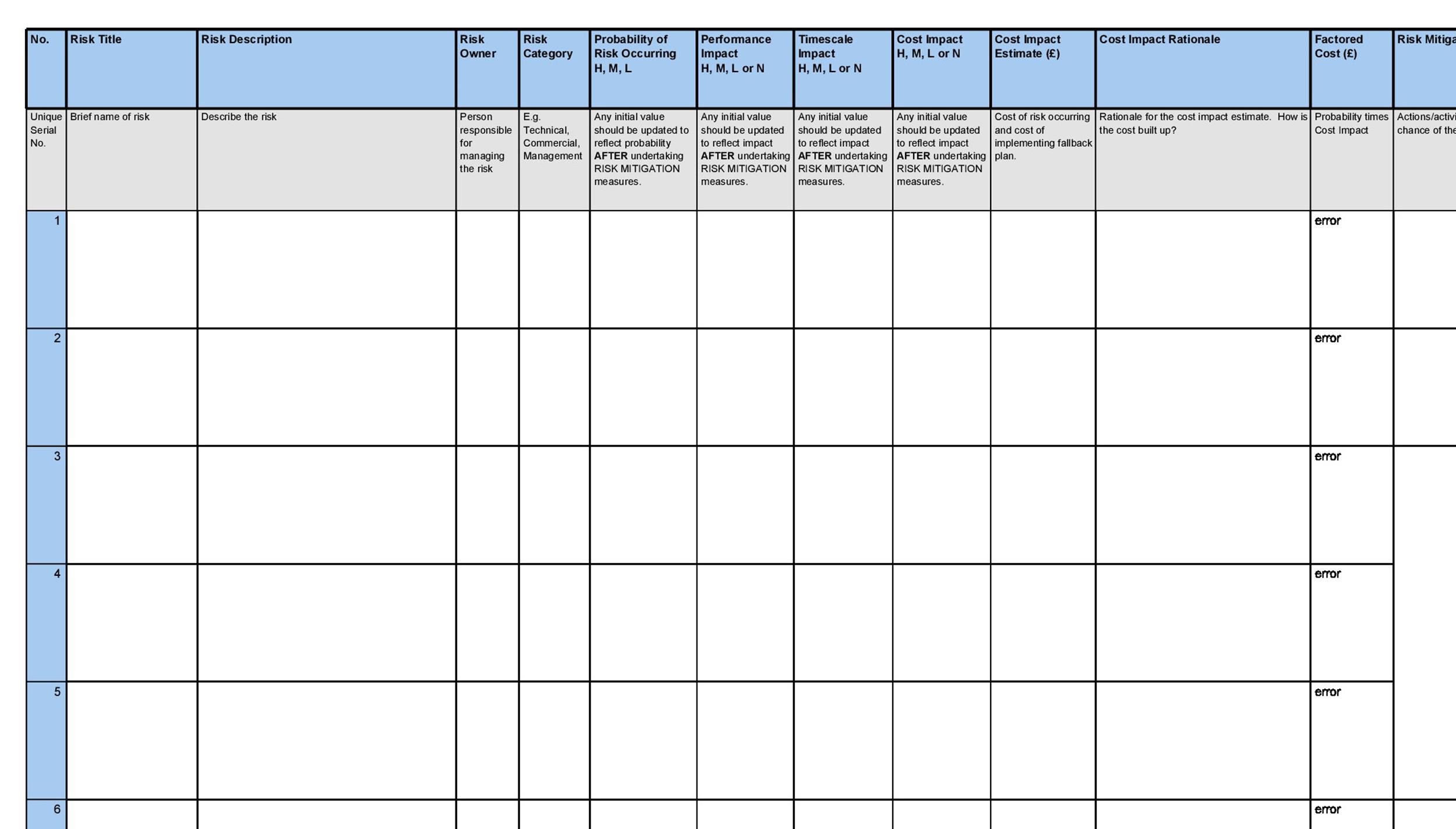
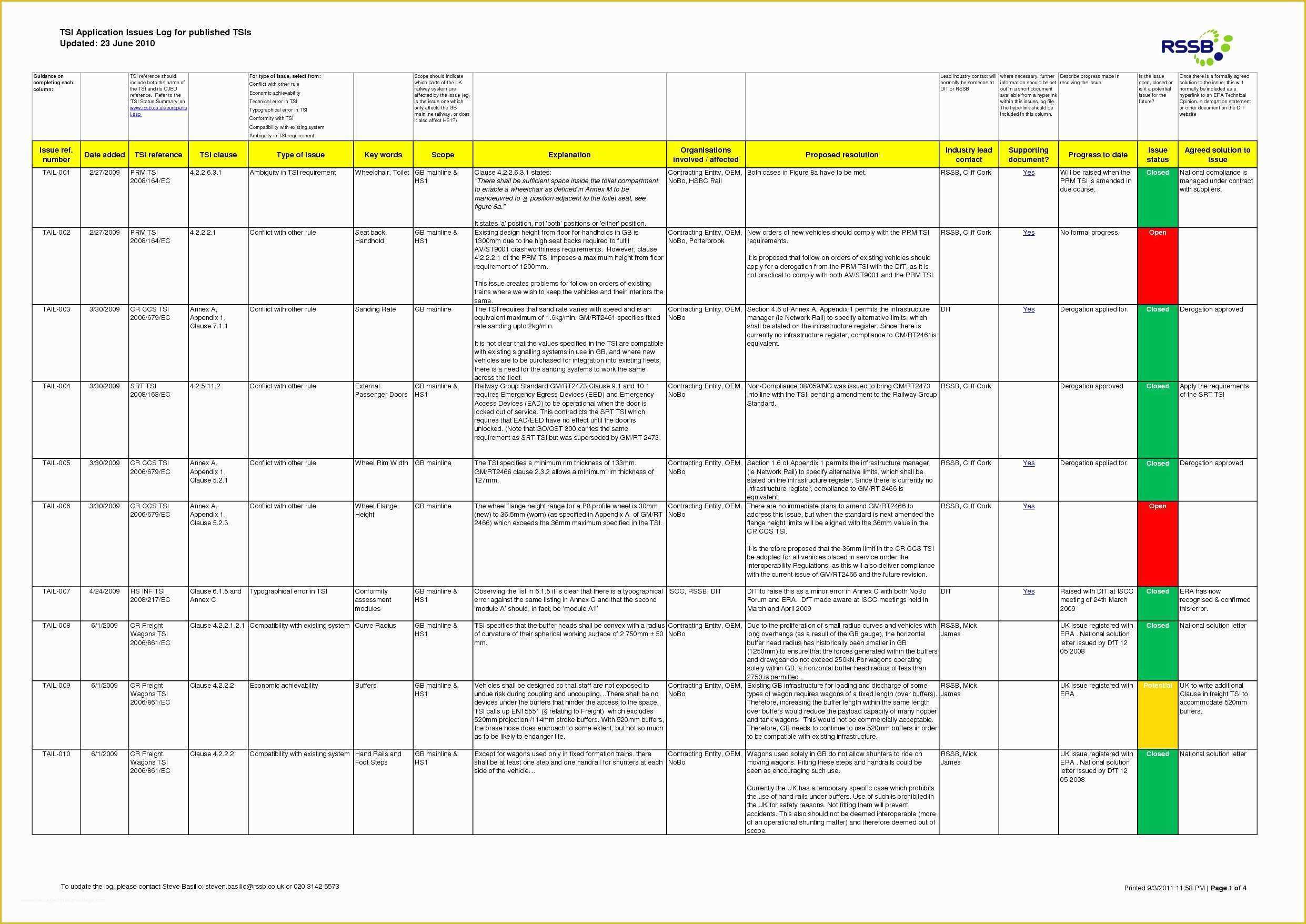
Information Security Risk Register Template
Information Security Risk Register Template - To make sure you’re starting on the right foot, we’ve provided a free, downloadable risk register template you can use once you have a. A cybersecurity risk register can help delegate across cybersecurity risk management, track risk owners, improve risk identification, streamline. An information security risk register is indispensable in cybersecurity for its role in preemptive threat management.
An information security risk register is indispensable in cybersecurity for its role in preemptive threat management. A cybersecurity risk register can help delegate across cybersecurity risk management, track risk owners, improve risk identification, streamline. To make sure you’re starting on the right foot, we’ve provided a free, downloadable risk register template you can use once you have a.
An information security risk register is indispensable in cybersecurity for its role in preemptive threat management. A cybersecurity risk register can help delegate across cybersecurity risk management, track risk owners, improve risk identification, streamline. To make sure you’re starting on the right foot, we’ve provided a free, downloadable risk register template you can use once you have a.
Risk Register Archives Adam M. Erickson
An information security risk register is indispensable in cybersecurity for its role in preemptive threat management. A cybersecurity risk register can help delegate across cybersecurity risk management, track risk owners, improve risk identification, streamline. To make sure you’re starting on the right foot, we’ve provided a free, downloadable risk register template you can use once you have a.
11+ Data Center Risk Assessment Template DocTemplates
A cybersecurity risk register can help delegate across cybersecurity risk management, track risk owners, improve risk identification, streamline. An information security risk register is indispensable in cybersecurity for its role in preemptive threat management. To make sure you’re starting on the right foot, we’ve provided a free, downloadable risk register template you can use once you have a.
Risk Register Examples for Cybersecurity Leaders
To make sure you’re starting on the right foot, we’ve provided a free, downloadable risk register template you can use once you have a. An information security risk register is indispensable in cybersecurity for its role in preemptive threat management. A cybersecurity risk register can help delegate across cybersecurity risk management, track risk owners, improve risk identification, streamline.
Cyber Security Risk Assessment Template Excel SexiezPicz Web Porn
An information security risk register is indispensable in cybersecurity for its role in preemptive threat management. A cybersecurity risk register can help delegate across cybersecurity risk management, track risk owners, improve risk identification, streamline. To make sure you’re starting on the right foot, we’ve provided a free, downloadable risk register template you can use once you have a.
Risk Register Template Excel Free And Information Security Risk
To make sure you’re starting on the right foot, we’ve provided a free, downloadable risk register template you can use once you have a. A cybersecurity risk register can help delegate across cybersecurity risk management, track risk owners, improve risk identification, streamline. An information security risk register is indispensable in cybersecurity for its role in preemptive threat management.
Risk And Opportunity Register Template Excel Track All Of Your Risks
A cybersecurity risk register can help delegate across cybersecurity risk management, track risk owners, improve risk identification, streamline. An information security risk register is indispensable in cybersecurity for its role in preemptive threat management. To make sure you’re starting on the right foot, we’ve provided a free, downloadable risk register template you can use once you have a.
Creating a Centralised Cyber Risk Register Vigilant Software
To make sure you’re starting on the right foot, we’ve provided a free, downloadable risk register template you can use once you have a. An information security risk register is indispensable in cybersecurity for its role in preemptive threat management. A cybersecurity risk register can help delegate across cybersecurity risk management, track risk owners, improve risk identification, streamline.
Sample 45 Useful Risk Register Templates Word & Excel Templatelab
A cybersecurity risk register can help delegate across cybersecurity risk management, track risk owners, improve risk identification, streamline. To make sure you’re starting on the right foot, we’ve provided a free, downloadable risk register template you can use once you have a. An information security risk register is indispensable in cybersecurity for its role in preemptive threat management.
45 Useful Risk Register Templates (Word & Excel) ᐅ TemplateLab
An information security risk register is indispensable in cybersecurity for its role in preemptive threat management. A cybersecurity risk register can help delegate across cybersecurity risk management, track risk owners, improve risk identification, streamline. To make sure you’re starting on the right foot, we’ve provided a free, downloadable risk register template you can use once you have a.
Information Security Risk Register Template
An information security risk register is indispensable in cybersecurity for its role in preemptive threat management. A cybersecurity risk register can help delegate across cybersecurity risk management, track risk owners, improve risk identification, streamline. To make sure you’re starting on the right foot, we’ve provided a free, downloadable risk register template you can use once you have a.
An Information Security Risk Register Is Indispensable In Cybersecurity For Its Role In Preemptive Threat Management.
To make sure you’re starting on the right foot, we’ve provided a free, downloadable risk register template you can use once you have a. A cybersecurity risk register can help delegate across cybersecurity risk management, track risk owners, improve risk identification, streamline.